Home Defence
Home defence. Get hard. Stay Happy
I wanted to write a post around securing your home network against attack. We protect our homes every year with CCTV, various Alarms, and protect ourselves against physical intrusion but what about all the electronic kit we have in our home, how are we exposing ourselves to Hackers? In this guide I’ll write about the problems I’ve faced & what I’ve done to get hard, and stay hard.
Our House (in the middle of our street)
We’re tech junkies in our house. Over the last 24 months we’ve installed a full Phillips Hue set, Hive off-shoots for various other bits of lighting, we have full blanket coverage of Google Home Assistant, and Sky Q with Wi Fi boxes along with IP cameras. Google’s set up with automatic payment details and all our services such as NetFlix, Spotify and others all configured, and all this kit (along with the myriad of iPads, Consoles, TVs and computers) were all sitting behind a domestic stock Sky Router!
In my career, I spend so much time advising others on how to be secure, as I added the seventh Google device into my home recently (damn those Black Friday deals!) I thought about how I really should protect the house from kerbside attack. Especially as if someone did get in, our Identities could be stolen in moments. Becca’s recently had her ID stolen and money taken from her account (another story) and I’ve recently hardened my online real-estate as I’ve been compromised so with protection in mind I looked at what I could do to get a bit more secure.
Think Like a Hacker
I also (as I went through this exercise) wondered if I could break into my home network. I cracked open a Knoppix Bootable CD, WireShark, AirSnort, LophtCrack and a range of other tools and sat in the car outside with a Pringles can and went to work like it was 1992.
My SSID was visible from outside, labelled by the stock Sky hub name, that told me I would have probably been using the stock Sky username & password, (I was). This didn’t shock me as I knew I was being lax, but to discover it so easy using off the shelf sniffing software was an eye opener. I sat and air snorted some packets and could see at least two Cameras on the network (including manufacturer and model number) an iPad, and the Google Assistant in the kitchen. I also saw the hub I had upstairs in the back office, and after enough time sure enough a grabbed a plain text password straight from the air for a laptop. Further browsing showed the public IP available on the router and after some forum searching on Sky I found an exploit I could have probably run to own the router.
I was also shocked at by changing my existing IP to the local subnet of the home network, I was able to browse directly to the camera feeds. Hmmm.. Not good.
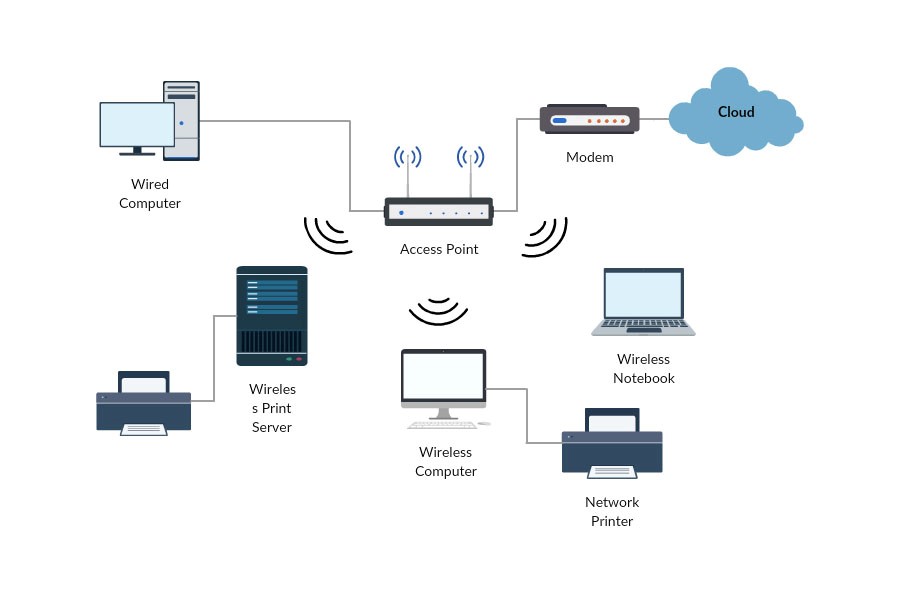
The Audit
The first thing I did was physically & then virtually audit the home. I drew a map of everything we have connected, where it sits and what it does. I then inspected the router admin console and looked at all the IP addresses, whether they were static or dynamically assigned via DHCP, I looked at the default IP range being used and things such as the exposure of the SSID for the Wifi. Once I had all this information I made a note of all the admin passwords for each bit of kit and listed all the connected services configured to be used with each device – this isn’t a small task.
 We had things such as;
We had things such as;
Netflix
Amazon Prime
Amazon One Click Payment
Amazon Dash buttons
Spotify
Sky Q
This was along with over 45 pieces of hardware, all with an assigned IP and all able to give out our information!
The Research
I then spent some time on the Sky forums and learning about the router itself. Should I put a firewall in the way? No, probably too much. What I wanted to know was things such as can I change the IP pool for internal devices? Can I mask the SSID of the Wifi network and can I encrypt the outside remote connection to the router.

The Hardening
With all this information I then went about hardening the network. I encrypted the connection to the router from outside, changing the stock username & password on the Sky router to something massively complex.
I then changed every internal device in the house’s class C IP (192.168.1.x) to a different class and I also made everything DHCP (there were some statics floating around). I then limited the pool.
Once that was done, I hid the SSID and changed the Wifi network name to something obscure (no ‘too Fly for a Wifi’ or ‘Sky HomeHub4564’ here which gives away far too much information.
Then it was onto each device. For each one I change the stock user names & passwords to something far more complex. I updated the firmware on everything, from the cameras’ to the router itself.
Passwords
With regards to the passwords I made sure everything was super complex and that goes for all the associated online accounts too. I used a password generator to generate them all. NB you have to be careful using password generators. Like domain name lookup tools, some online tools automatically pass all this information on to hackers and spammers, along with the sites are often compromised. The link above and something like LastPass will always serve you well. Just be careful!
Summary
- Never use the stock passwords
- Hide or at least obfuscate your SSID for your WiFi
- Change usernames from ‘Admin’ to something else on all hardware
- Ensure devices don’t broadcast unnecessarily
- Move any IP cams into a DMZ (you can do this even on domestic routers) and give them something other than a Class C subnet
- Set a limited range DHCP pool if using dynamic IP addressing (to help stop devices you aren’t aware of grabbing an IP). If you have ten devices, give your pool 10 etc.




